Information Security Management
Information security management system:
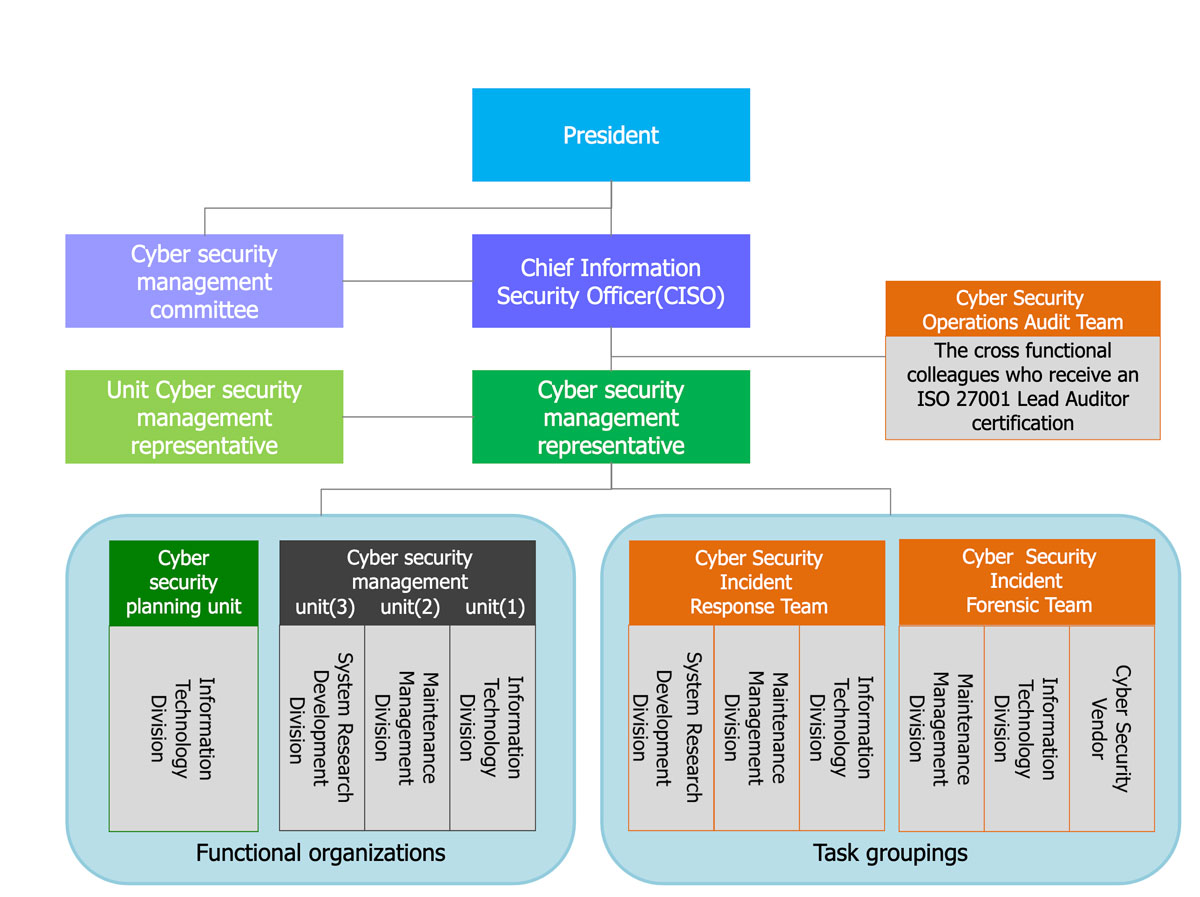
In order to ensure information security is effectively implemented within daily operation, the Corporation established an “Information Security Management Committee” to review information security goverance, strategies, and operations. The committee is convened by CISO(Chief Information Security Officer) and joined by Corporation Information Security Representative along with each department head acting as Information Security Management Committee members. Corporation Information Security Representative is responsible to manage and oversee the planning, promotion, and implementation of information security operation as well as compliance with Cyber Security Management Act、and Guidelines for Information and Communication Security Management for Exchange-Listed and OTC-Listed Companies. Implementation results were as follows:
1. The head of Information Technology Division acts as CISO and the chairman of the information security management audit meeting. Regular meetings are held every 6 months to assess information security developments and strategies, ensuring that information security management systems can continue to operate in a stable manner.
2. Each office and department unit assigned an information security representative, and the head of the System Operation Department in the Information Technology Division acts as the information security management representative. These representatives convened an “Information Security Representative Meeting” every quarter to report information security plans under development and implementation results, and to promote relevant information security policies and implementation highlights.
3. Relevant information security management report and implementation results were submitted to the 2nd board meeting of the 10th Board of Directors on June 06, 2023.
Information Security Management Structure
Specific management plans:
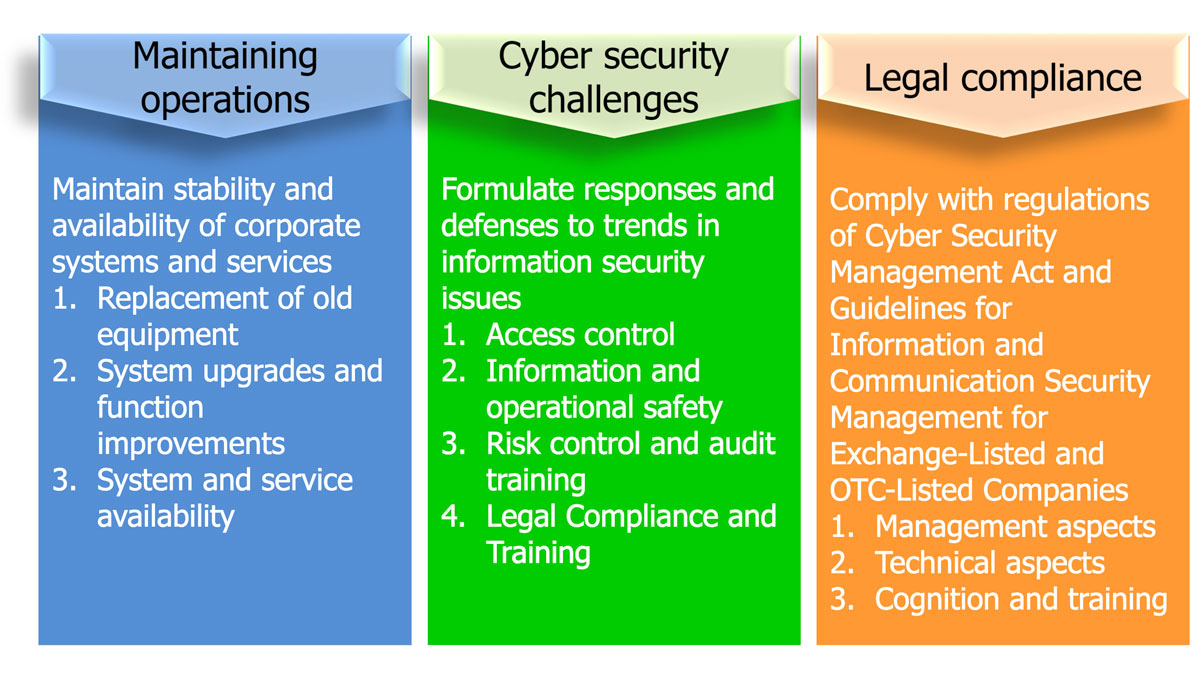
1. The Corporation has established its “Regulations for Governing Information Security” to ensure that our hardware, software, data, and personnel adhere to the principles of C (Confidentiality), I (Integrity), A (Accessibility), and C (legal Compliance). Our information security system is built on the three aspects of Maintain operations, Information security challenges, and Legal compliance, and we are gradually improving relevant management measures.
2. The Corporation took out electronics equipment insurance policies for operational assets relating to maintenance of information systems and network equipment; security monitoring measures and access control were in place to prevent incidents of theft and malicious destruction.
3. To implement Defense in depth, the Corporation is committed to deploy multi-layered information security protection on information services such as network, personal computers, servers, and data protection as well as committed to prevent any malignant cyber attack or hacking. However, the Corporation can neither claim nor guarantee total invincibility against cyber attacks such as APT (Advanced Persistent Threat) attacks, DDoS (Distributed Denial of Service) attacks, ransomware, social engineering attacks, and information theft that could result in disruption to information service systems. To shorten cybersecurity incident detection time, the Corporation implements SIEM(Security Information and Event Management) platform and SOC (Security Operation Center). The Corporation also evaluates taking on cyber-insurance as an additional backing. In light of the fact that cyber-insurance is a new type of insurance policies, and in consideration of all issues relating to insurance scope, claim scope for damages, identification of damages, and qualification of identification institutes, the Corporation decides to respond to current information security challenges through annual external audit & internal audit, internal control system, information security regulation review, and information security implementation procedure review. The following strategies have been adopted:
- Continued annual review of trends in information environments and technical information in accordance with our corporate information security policies, and establishment of protective measures and solutions.
- Implementation of annual security checks, information and communication security health checks, and social engineering and information breach scenario exercise to strengthen employee awareness of information security crises and response capabilities, in hopes of efficiently preventing and detecting threats and halting proliferation at the first instance.
- To strengthen employee awareness of information security crises and response capabilities, information security training to all employees are conducted quarterly as well as social engineering and information breach scenario exercise are conducted routinely.
- Establish cyber security incident notification and response protocols for incident notification to all related agencies, creating incident response team, assessing incident impact scope, conducting damage control, and post-incident investigation. The implementation of protocol minimizes impact on THSRC service coverage & service time, and prioritizes preserving passenger rights.
4. The Corporation has passed annual check for ISO27001 information security management systems in October 2025 Current ISO27001 certificate is valid from Dec. 28, 2023 to Dec. 27, 2026.

